Aldelo POS hacking
 Point-of-sale (POS) malware is an information security ailment that, within less than seven years, reached colossal proportions and became more damaging to organizations than almost any other threat. Although this threat is less sophisticated than malware like banking Trojans, it can be hugely destructive due to the following:
Point-of-sale (POS) malware is an information security ailment that, within less than seven years, reached colossal proportions and became more damaging to organizations than almost any other threat. Although this threat is less sophisticated than malware like banking Trojans, it can be hugely destructive due to the following:
- It directly affects many of a brand’s customers.
- It becomes public immediately after being discovered, usually by someone outside the victim organization.
- Its collateral damage involves customers, issuers, card associations and the victim’s own service providers (insurance, anyone?).
I would have collected some information about how much these card breaches cost the victim organizations, but after we all witnessed the Target breach — its detrimental financial results in both hard and soft costs, its damage to the brand and its executive team and the never-ending legal mess it is — I think we all get the point.
What Target was a victim of, as well as many other retailers and card processors that suffered a POS malware attack experienced, is the work of cybercriminals and organized cyber gangs who went after card data from customer transactions. The end goal is to rob the data and then use the card information in fraudulent purchases.
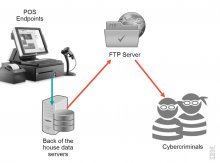
POS malware is actually a generic name for a growing number of Trojan families that are designed to scrape point-of-sale terminals’ RAM memory. It is designed to look for, grab and exfiltrate credit and debit card data from the endpoints that process and store it.
The notion of stealing payment card and PIN data is not new. Criminals always found card data to be highly lucrative and still use a number of real-world crimes to skim data in ATMs and card readers. They also try to compromise POS equipment installed at brick-and-mortar retailers to have the data stolen and streamed to them. Some criminals attempted sniffing data sent over Wi-Fi to back-of-the-house servers, but at the end of the day, all those physical crime scenarios demand deeper knowledge to tamper with the equipment and typically involve an insider.
You can easily infer that using POS malware is lucrative because it is considered a much safer and simpler way for cybercriminals to get their hands on large numbers of live payment cards without ever showing their face on security cameras.






