MalumPOS XL
 Last month, security researchers released a report about a targeted attack operation which they named Careto, or Mask in Spanish. The attack was noted for encoding its configuration data and encrypting its network traffic, making analysis more difficult.
Last month, security researchers released a report about a targeted attack operation which they named Careto, or Mask in Spanish. The attack was noted for encoding its configuration data and encrypting its network traffic, making analysis more difficult.
However, the capabilities of the Mac malware used in Careto was not as sophisticated as its Windows counterpart. (We detect this as OSX_CARETO.A.) It connects to a hardcoded command-and-control (C&C) server and runs /bin/sh to open a shell, which can then run commands sent from the C&C server. This particular backdoor is only approximately 88 kilobytes in size, which is not particularly large (especially since it contains both 32- and 64-bit code.) However, analysis of this malware is still not easy, due to the mentioned encoding and encryption. In this blog post, we look into the details of this encoding and encryption.

Figure 1. File structure of OSX_CARETO.A
Configuration Encoding
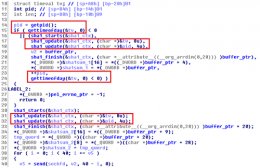
When this malware is run, it first decodes its configuration data. The encoding algorithm is pretty simple – every other byte is XORed with 0x7F and 0x10 alternately. Among the encoded information are its C&C server, a shared secret for network communication, and the program path for command shell. The C&C server used here is itunes212.appleupdt.com, which has now been sinkholed.
Figure 2. Configuration decoding
Figure 3. C&C Server
The malware then connects to its C&C server (which was found in the decoded configuration) and sends two 20-byte SHA1 checksums. These are used as part of the AES encryption keys later. The first SHA1 checksum is created using the time and the process ID (PID). The second SHA1 checksum is created in a similar way – by using a new timestamp and PID+1.
The encryption keys for sending and receiving are different. They are created by calculating the SHA1 checksum of a shared secret and the two SHA1 checksums mentioned earlier. All succeeding network traffic is encrypted with AES using these two keys.
Figure 4. Generate checksum
Figure 5. AES encryption key
Figure 6. Shared secret for network traffic
Command Shell
The malware then sends out a 16-byte message as a challenge. to the C&C server. If it gets a correct response from the C&C server, it creates a shell by opening /bin/sh. Attackers can then control this machines by sending commands, which are then executed in the opened shell window.